Algorithm For Mac
The main reason of using Process Flowchart or PFD is to show relations between major parts of the system. Process Flowcharts are used in process engineering and chemical industry where there is a requirement of depicting relationships between major components only and not include minor parts.
Process Flowcharts for single unit or multiple units differ in their structure and implementation. ConceptDraw PRO is Professional business process mapping software for making Process flowcharts, Process flow diagram, Workflow diagram, flowcharts and technical illustrations for business documents and also comprehensive visio for mac application. Easier define and document basic work and data flows, financial, production and quality management processes to increase efficiency of your business with ConcepDraw PRO.
Business process mapping software with Flowchart Maker ConceptDraw PRO includes extensive drawing tools, rich examples and templates, process flowchart symbols and shape libraries, smart connectors that allow you create the flowcharts of complex processes, process flow diagrams, procedures and information exchange. Process Flowchart Solution is project management workflow tools which is part ConceptDraw Project marketing project management software.
Drawing charts, diagrams, and network layouts has long been the monopoly of Microsoft Visio, making Mac users to struggle when needing such visio alternative like visio for mac, it requires only to view features, make a minor edit to, or print a diagram or chart. Thankfully to MS Visio alternative like ConceptDraw PRO software, this is cross-platform charting and business process management tool, now visio alternative for making sort of visio diagram is not a problem anymore however many people still name it business process visio tools. Flow chart is a diagrammatic representation of an algorithm and essential part of planning the system. Flow charts are widely used in technical analysis and programming for easy writing programs and explaining them to others. So, one of the most popular type of flow charts is Technical Flow Chart. Technical Flow Chart can be drawn by pencil on the paper, but it will be easier to use for designing a special software. ConceptDraw PRO diagramming and vector drawing software extended with Flowcharts Solution from the 'Diagrams' Area of ConceptDraw Solution Park will be useful for this goal.
Cross-Functional Flowchart is a type of chart which shows the series of process steps connected by the arrows to depict their order and applies the swim lanes to provide an extra dimension with means of assigning each process step to certain category. Often the category or the functional unit is a stakeholder (department, person, role), resource, project, phase, or any other attribute.
Cross-Functional Flowcharts visually illustrate relationships between the business processes and the functional units responsible for this processes. ConceptDraw PRO is a powerful diagramming and vector drawing software for professional design Cross-Functional Flowcharts using the common notation of shapes and swim lanes. Cross-Functional Flowcharts solution included to the Business Processes area of ConceptDraw Solution Park provides numerous well-designed vector objects and connector tools for quick, easy and effective organizing information, representing process flows and relationships, and drawing Cross-Functional Flowcharts for business, science, education, technology, etc. A flowchart maker is a software showing the interaction, sequence or organization. It also known as flowchart maker or ConceptDraw PRO standard supplied with different types of symbol collections: standard symbols, branded set and authored. It used strictly for enhancing scientific or business documents with abstract explanatory pictures. Business graphic applications show a special knowledge representations and include many features for creating schematic pictures.
These graphic tools are known as flowchart maker or flowchart maker software.
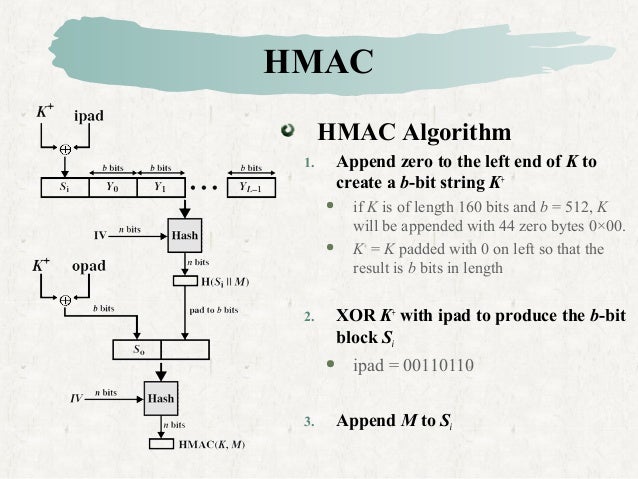
A is a completely public, deterministic hash function which everybody can compute over arbitrary inputs. It takes as input a sequence of bits (any sequence of bits; some hash functions are formally limited to inputs of, say, less 2 64 bits, aka '2 millions of terabytes') and outputs values in a rather small space, typically a sequence of bits with a fixed size (e.g. Always 160 bits with the standard hash function ). Good cryptographic hash functions respect some conditions which boil down to, informally, that they mix input data so thoroughly that we cannot figure it out afterwards. A is an algorithm which takes as input a message and a secret key and produces a fixed-sized output which can be later on verified to match the message; the verification also requires the same secret key.
Algorithm For Macd
Contrary to hash functions where everything is known and attackers are fighting against mathematics, MAC make sense in models where there are entities with knowledge of a secret. What we expect from a good MAC is unforgeability: it should be infeasible to compute a pair message+MAC value which successfully verifies with a given key K without knowing K exactly and in its entirety. Hash functions and MAC are thus distinct kind of algorithms with distinct properties and used in really distinct situations.
Some MAC algorithms (but certainly not all of them) can be thought of as 'hash functions with a key' but this is a restrictive view. Is a well-known MAC construction, which itself builds on an underlying hash function in a smart way. Indeed, security properties and models for hash functions and MAC are sufficiently distinct from each other that slapping a hash function and a key together does not necessarily yield a secure MAC, even if the hash function is secure (see the which illustrates that point). To some extent, we can state that a MAC algorithm which can operate securely without an must exhibit some hash-like properties (that's the reason I like HMAC: without an IV, it is much harder to get it wrong when implementing it).
Algorithm For Machine Learning
However, the Devil is in the details. They are two totally different primitives. A MAC is used for message authentication, and is a symmetrically keyed primitive. A hash function can be used for many purposes, and has no special key input. MAC is an acronym of 'message authentication code'. Don't be confused by the fact that some MAC algorithms (e.g., SHA1-HMAC) work by using a hash function as a subroutine. They're very different beasts.
Some examples of MAC algorithms: CMAC, SHA1-HMAC, MD5-HMAC, UMAC, Poly1305-AES. Some examples of cryptographic hash functions: SHA256, SHA1, MD5. Found this to the point answer from another forum.
These types of cryptographic primitive can be distinguished by the security goals they fulfill (in the simple protocol of 'appending to a message'): Integrity: Can the recipient be confident that the message has not been accidentally modified? Authentication: Can the recipient be confident that the message originates from the sender? Non-repudiation: If the recipient passes the message and the proof to a third party, can the third party be confident that the message originated from the sender? (Please note that I am talking about non-repudiation in the cryptographic sense, not in the legal sense.) Also important is this question: Keys: Does the primitive require a shared secret key, or public-private keypairs? I think the short answer is best explained with a table: Cryptographic primitive Hash MAC Digital Security Goal signature -+-+-+- Integrity Yes Yes Yes Authentication No Yes Yes Non-repudiation No No Yes -+-+-+- Kind of keys none symmetric asymmetric keys keys Please remember that authentication without confidence in the keys used is useless. For digital signatures, a recipient must be confident that the verification key actually belongs to the sender. For MACs, a recipient must be confident that the shared symmetric key has only been shared with the sender.